- Back to Home »
- Information , Networking »
- TCP / IP BASIC NETWORKING
Posted by : Beauty Cyber Squad Official
Tuesday, December 17, 2019
TCP/IP
We can assume that the networking model is a collection of documents. Each of these documents contains requirements for a network to function as well as logical rules (protocols).
What is protocol?
protocol is a standard used to define a method of exchanging data over a computer network, such as local area network, Internet, Intranet, etc. Each protocol has its own method of how to handle data in the following situations.
- How data is formatted when sent.
- What to do with data once received.
- How data is compressed.
- How to check for errors in the data.
Likely the most important protocol is TCP / IP (transmission control protocol / Internet protocol) which is used to govern the communications of every computer connected to the Internet. HTTP (Hypertext Transfer Protocol), which is used to transmit data over the world wide web (Internet), is "carried" by TCP / IP.
The analogy is, when we want to make a building, of course we need the name blueprint, how the foundation, internal design, external design, room layout, to the electrical grooves, gas, smoke removal, and so forth.
With the blueprint, all parties working on the building will be able to work well, from electricians, painters, interior designers, and so on have followed the same reference.
so, protocol is a way for each different device to communicate effectively with both software and hardware.
History About OSI and TCP / IP
In the past, there was no networking model, including TCP / IP. Each vendor makes their own proprietary standards, for example IBM with its networking model known as Systems Network Architecture (SNA) in 1974.
Likewise other vendors. That said, they compete with each other to create the best networking model so others use it.
Of course this is a bad state. So that the International Organization for Standardization (ISO) takes a role to overcome this, by creating standards that we are familiar with OSI.
In addition, there are also other organizations that develop standards with the same goals and with similar architectures, the Department of Defense (DoD). This model is known as TCP / IP or sometimes called the Dod Model.
At present, the world of computer networking refers to the same standard, namely TCP / IP.
Yup, not OSI.
The steps are roughly like this:

The history between TCP / IP and OSI is actually very long. I am also studying it and am still confused, for example with the question "which one was there, TCP / IP or OSI?"
You can leave a comment below if you know about this.
So that the comparison of TCP / IP and OSI is not discussed in depth at this time, but you can make the following references
1. Online: TCP/IP Guide
2. Book: Computer Networking - Kurose Ross or Computer Network - Andrew S Tanenbaum
3. or that explains the history and comparison between OSI and TCP / IP in more detail: Open Systems Networking - Piscitello and Chapin
Benefits of TCP / IP
Because the networking model used today is TCP / IP, internet products have now adopted TCP / IP.
For example, if you currently buy a flash drive, then the flash drive has implemented TCP / IP. This means you can use it on laptops, computers, on all different devices. or for example. When we want to build a new infrastructure.
Before there was TCP / IP, we had to buy devices that were one brand, from routers, switches, firewalls, servers, everything.
Now, not anymore.
Because current vendors can excel at router devices, but not so with firewalls. For example, we want to use a Cisco router and switch, but prefer to use the Palo Alto firewall.
No problem. We can implement routing protocols, link aggregation, etc. without compatibility constraints. Because everything is using TCP / IP.
Some things that 'might' become the cause of the choice of TCP / IP to be the Networking Model Standard
For some people, including me, knowing TCP / IP is the standard networking model chosen is an interesting thing.
In fact, the current OSI tends to be more familiar to some of us, in fact it has never been a standard networking model. Is that weird?
Instead, what is used is TCP / IP. Here are some reasons:
1. OSI is more formal, slow to develop, because it is done by certain people.
2. TCP / IP was developed by volunteers all over the world, of course the situation has reversed compared to OSI
1. OSI is more formal, slow to develop, because it is done by certain people.
2. TCP / IP was developed by volunteers all over the world, of course the situation has reversed compared to OSI
Before TCP / IP was actually used, every vendor still used their own proprietary protocol, and at that time TCP / IP was still limited to being the 'gateway'.
Starting in the 1990s until now, every device now has implemented TCP / IP. Once again, not OSI. (See Figure 1 above).
TCP / IP Using RFC Documents
Do you often hear the term RFC?
RFC or Request for Comment is an official document used by the Internet Engineering Task Force (IETF), the contents of which are drafts, reviews, which will later be reviewed by interested parties.
These proposals in RFC will later become internet standards, for example the Internet Protocol is defined in RFC791 and OSPF is defined in RFC 1247.
RFCs are numbered. The contents of the document are very detailed about a protocol, how it works, usage procedures, concepts, and so on.
Not only formal review, even RFC can contain humor because everyone can submit anything to RFC, you can also do it through RFC Editor.
This is also one of the factors that makes TCP / IP more developed than OSI.
TCP/IP Layer
For example Ethernet LAN.
Ethernet LAN has been defined by the IEEE (Institute of Electrical and Electronic Engineers (IEEE), so TCP / IP no longer defines it in RFC, but refers to IEEE.
But..
Still, many, complex.
Here are some examples of mainstream protocols: HTTP, TCP, UDP, OSPF, EIGRP, BGP, OSPF, IPv4, RIP, and many more.
It will all make us dizzy.
This means, it is not a good way to understand TCP / IP starting with the protocol.
Well, there is an easier way to understand TCP / IP.
This is where the layer functions, or what we know as layers.

TCP / IP now has 5 layers, the difference lies in the division of layer 1 (link) original TCP / IP into Data Link and Physical in TCP / IP updated.
But for now, let's say we are referring to the original TCP / IP layer with 4 layers.
With this TCP / IP layer, many of the protocols will be categorized by function.
Some are in layer 1, layer 2, layer 3, and layer 4. So that we more easily understand it.
So like this:

There are a lot of protocols. But what we are talking about now is just like in the right hand column as shown in the picture, namely HTTP, TCP, UDP, IP, and Ethernet.
Maybe you can already guess, we will use a general sample: "When someone opens a browser, and accesses a web page".
Yup, this is a case study.
before we begin. Don't get me wrong about TCP, IP, and TCP / IP.
TCP, and IP, are 2 different protocols which I will explain below. Whereas TCP / IP is a networking model. Because it contains many protocols, it is also called a protocol suite.
Let's start.
#1. TCP/IP Application Layer
The application layer function only provides services to applications running on the computer. Remember, only the service, not the application.
For example, the FTP application protocol is Filezilla. or the HTTP application protocol is a web browser, which we know the most today. Despite the fact that the browser can not only be done with such applications, it can also be with a terminal for example on linux.
Now the task of the application layer here is to define how a browser can retrieve content from a web server to finally appear in a web browser.
The following explains the HTTP mechanism in more detail.
Imagine someone opening a web browser and accessing a web. The simple process would be something like this.

For example when you open this site, you will get a page from https://beautycybersquad.blogspot.com which is the homepage.
Regarding https or Hypertext Transfer Protocol Secure is a secure version of HTTP, because it uses SSL or Secure Socket Layer. Sometimes referred to as SHTTP or S-HTTP.
The goal is that communication occurs safely because the data sent will be encrypted. This is especially important on buying and selling sites where users enter confidential data such as credit cards.
HTTP mechanism
Above that the simplest example or we call the basic logic of the HTTP process. Technically it's not like that.
In the mid 1990s, Barner Lee created HTTP, a web browser and web server. HTTP here provides the ability for web browsers to request content from a web server.
Likewise with the web server, with HTTP he can provide the content requested by the client.
The process is like this:

Protocol uses headers to store information. From the HTTP mechanism above we can see 3 processes that occur when a client requests a web page from the server.
1. GET Header: Suppose the client accesses https: /beautycybersquad.blogspot.com, meaning the server will send its homepage. Likewise if you access a specific URL.
2. GET Reply: the server responds to the header from the client, and replies to it first with the HTTP Header "OK" to continue sending part of the homepage. This if successful, then the header will be worth "200", besides that for example "404" which we are familiar with not found.
3. HTTP Data: because the communication has already been initialized, the server continues to send the contents of home.html, more effective than sending headers over and over again.
If we look at the process from
If we look at the process of the application layer, then at a glance the process is complete and simple. Though there are so many more processes that occur, namely in the layers below it.
#2. TCP/IP Transport Layer
The transport layer on TCP / IP is also called Host-to-Host, its function is to establish connections between hosts. For example between one computer with another, client and server. There are many protocols that are at the transport layer, but the most we know in general are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). Returning to the HTTP process above, we access the website of course want reliable data.
What does reliable mean?
In fact, sending data from one computer to another is a complex process, and has many procedures. There are several factors that cause data to fail to be sent.
Imagine that you are currently reading this site with a network that is often disrupted, so that there are missing paragraphs, there are only half titles, or letters of words that are lost in the middle of paragraphs.
Bad right? This is where TCP is needed.
* Transmission Control Protocol
At this point we agree that the HTTP communication above runs using TCP. This means that HTTP requires guarantees that data can be sent perfectly. When data fails to be sent, the recipient must be aware that it is happening, and request a retransmission.
The trick is like this: TCP breaks up the data (segment) and then sends it based on the Sequence number (SEQ).
TCP also has many functions, but our focus is only on one of the best known main functions, namely TCP Error Recovery.

Like this the process:
1. The server is sending segments with several client number sequences.
2. but in seq 2, the segment failed to send.
3. After the client receives all the data, it turns out that something is lost. Then the client asks the server to send back the lost segment in seq 2.
Three-Way Handshake TCP
Don't think that when you enter the address of this site in the browser, the laptop that you use will immediately receive the contents of this site. Not.
When a client enters a url address in a web browser, the client requests a server to establish a connection, called an establishing connection. This is why TCP communication is called connection oriented. The establishment of this connection will form a virtual link. Virtual path used for segment delivery.

In other words, the sender and receiver agree first to make the transmission. After both agree, a connection is made, followed by sending data. In the process of sending data, TCP Error Recovery is needed, which I have explained above.
So the plot: Establishment of Connection -> Data Transmission (with error recovery).
User Datagram Protocol (UDP)
The question is, do all host-to-hosts use TCP?
Not always. Because not all communications require reliable data transmission. For example: voice communication.
"When we call, it is not uncommon for our voices to not reach the other person because of connection problems. Imagine if a few seconds later, the voice reaches the other person. "
Surely this is annoying
So there are considerations why use UDP over TCP:
1. Need fast communication
2. No need to form a connection first
3. No need for error recovery
All of the above are the opposite of TCP criteria.
We return to the case study. What actually happens when the client enters the URL address in the browser? Does a TCP connection occur immediately, then sending HTTP data?
The answer is no. It turns out there is still one more process.
The inputted URL is for example: https://beautycybersquad.blogspot.com, this is the domain. The computer cannot recognize this name. So to recognize it, you need DNS or Domain Name System.
The Domain Name System is a protocol used to translate domain addresses (for example: ngonfig.net) into IP addresses.

The DNS server already has a list of domains and their IP addresses. If at any time someone asks, then he just sends, and without any process to ensure the message is received by the client. There is also no connection before the data is sent.
Until here I hope you have understood the difference between TCP and UDP.
after the IP address is known by the client, the client requests a connection to the IP. So in the processes that I have explained above, the communication is no longer directed to the domain address, but rather the IP address.
Summary of the flow: Input URL -> Ask the IP address of a domain -> Make a connection request to the IP that has been obtained -> Perform data transmission.
This IP address will be discussed at the network layer below.
#3. TCP/IP Internet Layer
Now we discuss layer 3, or often called the Network Layer. At the network layer or internet layer there are also many protocols. But, the only, the most known and used today, namely: IP or Internet Protocol. Here I will not describe the types of IP addresses, classes, what is a network, and what is a host. we will only discuss the concept.
Analogy to the Internet Protocol and Post Office
Imagine now you want to send letters to 2 different destinations, local and international, namely Jakarta and Singapore. all you have to do is write the destination address of the letter and put it in the post office box or you can deliver it directly to the post office. We do not need to think and do not need to regulate how and which paths must be taken by the delivery of the letter in order to reach the destination.

We know, the post office has many branches in every city and every area that often occurs shipping. Like the picture, it turns out the path taken by the two letters is different. Because, the first: the letter sent earlier will be distinguished destination address. Then separated based on the closest office, there is also a separation based on the destination of each shipment. There must be sent first to the regional office, some are sent directly to the destination address.
Then, what to do with IP?
Remember I said about the two letters, some were sent to the office first, some were sent directly to the destination? This is because the post office already has a list of addresses and routes. Then the letter may not arrive if we do not include the address.
The division of this address, we differentiate into 2:
1. Network address: for example, the Jakarta area. This can be considered a postal code.
2. Host address: apparently there is West Jakarta, East Jakarta, and so on. This can be thought of as a shipping detail address, for example a house number.
After understanding the analogy, we proceed to the case study. This time I differentiate DNS servers from HTTP servers.
 Remember the analogy, Internet Protocol defines two things in the IP Address. Look at the picture above:
Remember the analogy, Internet Protocol defines two things in the IP Address. Look at the picture above:
1. Each IP owned by the host must be unique, 2.2.2.2, 3.3.3.3, and 1.1.1.1
2. these IP addresses must also be grouped, for example 2.0.0.0, 3.0.0.0 and 1.0.0.0
Then it goes like this:


Do you often hear the term RFC?
RFC or Request for Comment is an official document used by the Internet Engineering Task Force (IETF), the contents of which are drafts, reviews, which will later be reviewed by interested parties.
These proposals in RFC will later become internet standards, for example the Internet Protocol is defined in RFC791 and OSPF is defined in RFC 1247.
RFCs are numbered. The contents of the document are very detailed about a protocol, how it works, usage procedures, concepts, and so on.
Not only formal review, even RFC can contain humor because everyone can submit anything to RFC, you can also do it through RFC Editor.
This is also one of the factors that makes TCP / IP more developed than OSI.
TCP/IP Layer
For example Ethernet LAN.
Ethernet LAN has been defined by the IEEE (Institute of Electrical and Electronic Engineers (IEEE), so TCP / IP no longer defines it in RFC, but refers to IEEE.
But..
Still, many, complex.
Here are some examples of mainstream protocols: HTTP, TCP, UDP, OSPF, EIGRP, BGP, OSPF, IPv4, RIP, and many more.
It will all make us dizzy.
This means, it is not a good way to understand TCP / IP starting with the protocol.
Well, there is an easier way to understand TCP / IP.
This is where the layer functions, or what we know as layers.

TCP / IP now has 5 layers, the difference lies in the division of layer 1 (link) original TCP / IP into Data Link and Physical in TCP / IP updated.
But for now, let's say we are referring to the original TCP / IP layer with 4 layers.
With this TCP / IP layer, many of the protocols will be categorized by function.
Some are in layer 1, layer 2, layer 3, and layer 4. So that we more easily understand it.
So like this:

There are a lot of protocols. But what we are talking about now is just like in the right hand column as shown in the picture, namely HTTP, TCP, UDP, IP, and Ethernet.
Maybe you can already guess, we will use a general sample: "When someone opens a browser, and accesses a web page".
Yup, this is a case study.
before we begin. Don't get me wrong about TCP, IP, and TCP / IP.
TCP, and IP, are 2 different protocols which I will explain below. Whereas TCP / IP is a networking model. Because it contains many protocols, it is also called a protocol suite.
Let's start.
#1. TCP/IP Application Layer
The application layer function only provides services to applications running on the computer. Remember, only the service, not the application.
For example, the FTP application protocol is Filezilla. or the HTTP application protocol is a web browser, which we know the most today. Despite the fact that the browser can not only be done with such applications, it can also be with a terminal for example on linux.
Now the task of the application layer here is to define how a browser can retrieve content from a web server to finally appear in a web browser.
The following explains the HTTP mechanism in more detail.
Imagine someone opening a web browser and accessing a web. The simple process would be something like this.

For example when you open this site, you will get a page from https://beautycybersquad.blogspot.com which is the homepage.
Regarding https or Hypertext Transfer Protocol Secure is a secure version of HTTP, because it uses SSL or Secure Socket Layer. Sometimes referred to as SHTTP or S-HTTP.
The goal is that communication occurs safely because the data sent will be encrypted. This is especially important on buying and selling sites where users enter confidential data such as credit cards.
HTTP mechanism
Above that the simplest example or we call the basic logic of the HTTP process. Technically it's not like that.
In the mid 1990s, Barner Lee created HTTP, a web browser and web server. HTTP here provides the ability for web browsers to request content from a web server.
Likewise with the web server, with HTTP he can provide the content requested by the client.
The process is like this:

Protocol uses headers to store information. From the HTTP mechanism above we can see 3 processes that occur when a client requests a web page from the server.
1. GET Header: Suppose the client accesses https: /beautycybersquad.blogspot.com, meaning the server will send its homepage. Likewise if you access a specific URL.
2. GET Reply: the server responds to the header from the client, and replies to it first with the HTTP Header "OK" to continue sending part of the homepage. This if successful, then the header will be worth "200", besides that for example "404" which we are familiar with not found.
3. HTTP Data: because the communication has already been initialized, the server continues to send the contents of home.html, more effective than sending headers over and over again.
If we look at the process from
If we look at the process of the application layer, then at a glance the process is complete and simple. Though there are so many more processes that occur, namely in the layers below it.
#2. TCP/IP Transport Layer
The transport layer on TCP / IP is also called Host-to-Host, its function is to establish connections between hosts. For example between one computer with another, client and server. There are many protocols that are at the transport layer, but the most we know in general are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). Returning to the HTTP process above, we access the website of course want reliable data.
What does reliable mean?
In fact, sending data from one computer to another is a complex process, and has many procedures. There are several factors that cause data to fail to be sent.
Imagine that you are currently reading this site with a network that is often disrupted, so that there are missing paragraphs, there are only half titles, or letters of words that are lost in the middle of paragraphs.
Bad right? This is where TCP is needed.
* Transmission Control Protocol
At this point we agree that the HTTP communication above runs using TCP. This means that HTTP requires guarantees that data can be sent perfectly. When data fails to be sent, the recipient must be aware that it is happening, and request a retransmission.
The trick is like this: TCP breaks up the data (segment) and then sends it based on the Sequence number (SEQ).
TCP also has many functions, but our focus is only on one of the best known main functions, namely TCP Error Recovery.

Like this the process:
1. The server is sending segments with several client number sequences.
2. but in seq 2, the segment failed to send.
3. After the client receives all the data, it turns out that something is lost. Then the client asks the server to send back the lost segment in seq 2.
Three-Way Handshake TCP
Don't think that when you enter the address of this site in the browser, the laptop that you use will immediately receive the contents of this site. Not.
When a client enters a url address in a web browser, the client requests a server to establish a connection, called an establishing connection. This is why TCP communication is called connection oriented. The establishment of this connection will form a virtual link. Virtual path used for segment delivery.

In other words, the sender and receiver agree first to make the transmission. After both agree, a connection is made, followed by sending data. In the process of sending data, TCP Error Recovery is needed, which I have explained above.
So the plot: Establishment of Connection -> Data Transmission (with error recovery).
User Datagram Protocol (UDP)
The question is, do all host-to-hosts use TCP?
Not always. Because not all communications require reliable data transmission. For example: voice communication.
"When we call, it is not uncommon for our voices to not reach the other person because of connection problems. Imagine if a few seconds later, the voice reaches the other person. "
Surely this is annoying
So there are considerations why use UDP over TCP:
1. Need fast communication
2. No need to form a connection first
3. No need for error recovery
All of the above are the opposite of TCP criteria.
We return to the case study. What actually happens when the client enters the URL address in the browser? Does a TCP connection occur immediately, then sending HTTP data?
The answer is no. It turns out there is still one more process.
The inputted URL is for example: https://beautycybersquad.blogspot.com, this is the domain. The computer cannot recognize this name. So to recognize it, you need DNS or Domain Name System.
The Domain Name System is a protocol used to translate domain addresses (for example: ngonfig.net) into IP addresses.

The DNS server already has a list of domains and their IP addresses. If at any time someone asks, then he just sends, and without any process to ensure the message is received by the client. There is also no connection before the data is sent.
Until here I hope you have understood the difference between TCP and UDP.
after the IP address is known by the client, the client requests a connection to the IP. So in the processes that I have explained above, the communication is no longer directed to the domain address, but rather the IP address.
Summary of the flow: Input URL -> Ask the IP address of a domain -> Make a connection request to the IP that has been obtained -> Perform data transmission.
This IP address will be discussed at the network layer below.
Note: VoIP is not fully UDP, but also uses RTP for sequencing. DNS also requires TCP if the data size exceeds the UDP pool.
#3. TCP/IP Internet Layer
Now we discuss layer 3, or often called the Network Layer. At the network layer or internet layer there are also many protocols. But, the only, the most known and used today, namely: IP or Internet Protocol. Here I will not describe the types of IP addresses, classes, what is a network, and what is a host. we will only discuss the concept.
Analogy to the Internet Protocol and Post Office
Imagine now you want to send letters to 2 different destinations, local and international, namely Jakarta and Singapore. all you have to do is write the destination address of the letter and put it in the post office box or you can deliver it directly to the post office. We do not need to think and do not need to regulate how and which paths must be taken by the delivery of the letter in order to reach the destination.

We know, the post office has many branches in every city and every area that often occurs shipping. Like the picture, it turns out the path taken by the two letters is different. Because, the first: the letter sent earlier will be distinguished destination address. Then separated based on the closest office, there is also a separation based on the destination of each shipment. There must be sent first to the regional office, some are sent directly to the destination address.
Then, what to do with IP?
Remember I said about the two letters, some were sent to the office first, some were sent directly to the destination? This is because the post office already has a list of addresses and routes. Then the letter may not arrive if we do not include the address.
The division of this address, we differentiate into 2:
1. Network address: for example, the Jakarta area. This can be considered a postal code.
2. Host address: apparently there is West Jakarta, East Jakarta, and so on. This can be thought of as a shipping detail address, for example a house number.
After understanding the analogy, we proceed to the case study. This time I differentiate DNS servers from HTTP servers.
 Remember the analogy, Internet Protocol defines two things in the IP Address. Look at the picture above:
Remember the analogy, Internet Protocol defines two things in the IP Address. Look at the picture above:1. Each IP owned by the host must be unique, 2.2.2.2, 3.3.3.3, and 1.1.1.1
2. these IP addresses must also be grouped, for example 2.0.0.0, 3.0.0.0 and 1.0.0.0
Then it goes like this:
- Client wants to know the IP address of the domain https://ngonfig.net, then send a query first to the DNS Server, until the network layer, IP communication occurs between 1.1.1.1 with 2.2.2.2 (DNS Server).
- After the IP address is obtained, client 1.1.1.1 establishes a TCP connection for sending HTTP data to server 3.3.3.3 (HTTP Server)
it is the router that determines these directions. This is like the post office. If the network is different, the packet will be forwarded to the router next to it that is connected to the address.
Basics of the IP Routing Process
We repeat the process that has happened above: first, the client looks for an IP web server, after that HTTP communication will be initiated by establishing a connection. During the HTTP communication process, surely the message sent here already has a header. Now in this header there is IP address information, i.e. source IP and destination IP.

The picture above we refer to as ip routing (routing), so that the network has a list of routes to reach certain areas. Here we discuss the basics.
When the packet is sent, this is what happens:
- Client will compare beforehand, whether 3.3.3.3 one area with it or not. In this case, no. So he sent it to R1.
- The role of R1 is where we call it the gateway. R1 knows that 3.3.3.3 is the area connected to R2, then the packet is forwarded to R2
- Until R2, the packet was sent directly to 3.3.3.3 (server).
In essence, what is seen first is the region (network address), then the specific address (host address).
# 4. TCP / IP Link Layer (Data Link and Physical
Now it's the Link Layer (Data Link and Physical) turn to do their job.
In original TCP / IP, data links and physical are still combined, meaning both protocol and hardware are here. Whereas in TCP / IP updated already distinguished. Simply put, the link is the term used to refer to the path between nodes that are interconnected. The data sent is the value of bits, in physical, and frames in the data link. Then the IP packet formed at the network layer will be wrapped again like this:

- Client mengenkapsulasi IP packet dan berada diantara Ethernet header dan Ethernet trailer, ini akan menciptakan Ethernet frame.
- This Ethernet frame is transmitted using bit signals through the connecting media
- R1 receives the bits signal and translates it into an ethernet frame.
- When the ethernet frame is formed, the ethernet header and ethernet trailer are discarded, leaving an IP packet. Done ...
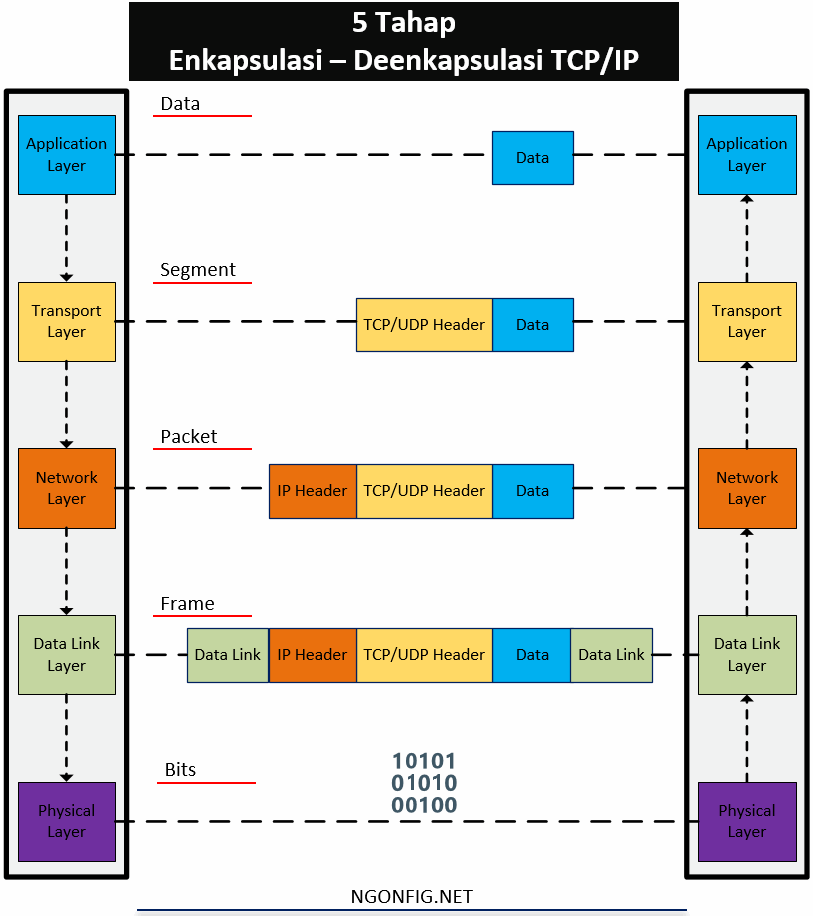
Data encapsulation in TCP / IP
Well, actually above I have explained the process of encapsulation and deencapsulation. To facilitate understanding, let's summarize the process. Above I have explained how HTTP, TCP - UDP, IP, and Ethernet do their job. Each of these layers will add a header (in the data-link, there is a trailer) of the data received from the layer above it. The server encapsulates the contents in the HTTP header. Then the TCP layer encapsulates the HTTP header into the TCP header. Then IP encapsulates the TCP header into the IP header. and finally at the Ethernet link layer, encapsulated IP packets into headers and trailers. This we call frames. Until then sent in the form of bit signals through the connecting media.
TCP / IP Case Study Summary - Encapsulation and Deencapsulation (5 Steps)
Stage 1:
Form and encapsulate application data with the required application header layer. For example the 200 message (OK) on HTTP that is replied by the HTTP header, and is followed by some web content
Stage 2:
Encapsulates data from the application layer to the transport layer header. Here use TCP for HTTP or UDP for DNS.
Stage 3:
Data from the transport layer is encapsulated into the IP header.
Stage 4:
The IP Header is then encapsulated by wrapping it with ethernet header and ethernet trailer.
Stage 5:
Send a bit signal, which will be translated by the receiving device, and produce an ethernet frame again, and deencapsulation is carried out.
Encapsulation of TCP/IP Deencapsulation

Congratulations!
You already understand one of the most important basic foundations in computer networks.











